Two-factor authentication (2FA) is an extra layer of protection for online accounts that requires you to use more than just your username and password to log in.
With 2FA enabled, you can protect access to your online accounts even if your passwords are leaked. We explain what 2FA is, how it works, and why you should use it wherever you can to protect your privacy and security online.
- What is two-factor authentication (2FA)?
- Why use 2FA?
- How does 2FA work?
- Types of 2FA
- What’s the difference between 2FA and MFA?
- How to enable 2FA
- 2FA backup codes
- Is 2FA secure?
- Use 2FA everywhere
What is two-factor authentication (2FA)?
Two-factor authentication (2FA), also known as two-step verification, is a security process that requires two forms of identification when you log in to an online account. Instead of just using your username and password to sign in, 2FA requires you to verify your identity again to access your account.
Once you’ve entered your password, you might have to enter a code generated by an authenticator app on your phone, plug in a physical security key, or use another method to prove it’s you logging in.
If you’ve ever been sent an SMS text with a passcode to log in to a website after entering your username and password, that’s a kind of 2FA.
Why use 2FA?
Passwords aren’t enough to protect your online accounts. Many people still use a single, easy-to-guess password for many accounts. But even if you use strong, unique passwords for all your accounts, your passwords could still be leaked in a data breach.
As data breaches are increasingly common and billions of passwords have been leaked(new window) in recent years, there’s a chance some of yours might be among them. Here’s how to check if your email or passwords have been revealed.
Similarly, phishing attacks are on the rise(new window) and becoming increasingly targeted, so even seasoned IT pros can fall victim. Scammers could trick you into entering your password on a fake website.
With 2FA enabled, if a password is ever cracked or revealed through phishing or a data breach, your online account will remain secure.
How does 2FA work?
2FA requires you to verify your identity twice when you log in — first with your username/password and then with something extra like a one-time security code or fingerprint.
Two-step verification
Here are the basic steps for 2FA, though the details vary by website, app, and the authentication method used:
- When you visit a website or open an app, you’re asked to enter your username and password to log in.
- The site or app’s servers recognize your username and password.
- You’re then asked for a second form of authentication, like a one-time security code, a fingerprint, a physical key you plug in, or some other method.
- Once you’ve passed the second authentication process — by providing the correct security code, fingerprint, etc. — you’re given access to your account.
In short, with 2FA you need to provide your username/password and one other way to verify your identity, known as an authentication factor.
What are authentication factors?
In 2FA, authentication factors are the ways you can prove it’s you trying to log in. There are three main types of authentication factors used for online consumer accounts:
- Something you know (knowledge factor): a password or passphrase, personal identification number (PIN), or answer to a security question
- Something you have (possession factor): a physical security key, mobile phone, or smart ID card
- Something you are (inherence factor): your fingerprint, face, iris, retina, or other biometric data

Some apps and websites may use two other factors to secure accounts:
- Where you are (location factor): the place you’re trying to log in from, for example, as determined by your IP address(new window) or GPS on your mobile phone
- What time it is (time factor): the time you’re trying to log in or the time you’re taking to log in, based on the assumption that logging in takes a limited, predictable time.
When you enable 2FA for an online account, if a criminal discovers just one of these factors, like your password, they’ll be out of luck. They’ll need a second factor to access your account.
Types of 2FA
Websites and apps offer different ways to secure your account with 2FA, and not all are equally secure. Here are the five main types of 2FA and the pros and cons of each.
SMS or voice-based 2FA
When you enable 2FA by SMS, you need to provide a mobile phone number. Next time you log in, you’ll be asked to enter a five- or six-digit one-time passcode (OTP) that’s texted to your phone after you enter your username and password. Or you may be told the code via a voice message sent to your phone.
Although it’s easy to set up and use SMS for 2FA, we don’t recommend it at all because:
- SMS messaging is unencrypted and inherently insecure. Hackers have found multiple ways to bypass 2FA by SMS, including hacking into the SS7 network to intercept 2FA codes and redirecting phone numbers with SIM swap attacks(new window).
- You have to reveal your phone number to the website or app.
- If you’ve set up your mobile number as a password-reset method, a criminal could potentially access your account without knowing the password.
Authenticator apps
The most popular type of 2FA involves using an authenticator app on your phone or computer to generate a time-based one-time passcode (TOTP). The app generates a new six-digit passcode (also known as a software token) every 30 to 60 seconds.

To use an authenticator app, you need to:
- Download and install a free 2FA app on your phone or computer. Popular authenticator apps include Authy, Google Authenticator, and FreeOTP.
- Set up the app for each account by scanning a QR code and entering a passcode in the website or app.
From then on, you’ll be asked to enter the current six-digit passcode from the app after entering your username and password to log in.
Using an authenticator app for 2FA is both more secure and more convenient than SMS and voice-based 2FA because:
- You can use it without a mobile signal as the codes are generated on your device.
- Unlike SMS 2FA, if someone redirects your phone to their number, they can’t access your 2FA codes.
However, if your phone is stolen or breaks, you’ll also be locked out of your accounts. So make sure you keep 2FA backup codes where they’re available.
2FA security keys
A third option for 2FA is to use a physical security key, also known as a hardware token. After you’ve entered your username and password, you’ll be asked to plug in a small USB device and press or touch a button on it to access your account.
Made in all shapes and sizes, most 2FA keys are similar to USB thumb drives or key fobs, like this YubiKey by Yubico.

Widely considered one of the most secure 2FA methods, security keys are also convenient. You don’t need to pull out your mobile phone and open an authenticator app every time you log in.
Like most popular 2FA keys, YubiKeys follow the FIDO U2F and FIDO2 authentication standards.
To use a security key, you’ll need to:
- Buy a key and register it with the website or app you want to use it with.
- After entering your username and password, you’ll be prompted to plug in the key and usually press or touch a button to log in. For example, you’ll have to touch the “Y” on the YubiKey above.
To use security keys with mobile phones, you first need to check if your phone or its operating system supports it. For example, Apple introduced support for security keys with iOS 16.3, released in January 2023.
Then, you can either plug in the key (if you have a compatible key) or tap the phone on the key (if the phone and key are NFC(new window)-enabled).

While far from all sites offer 2FA with security keys, it’s becoming increasingly popular and is considered one of the most secure options for 2FA. The main downsides with security keys are:
- You need to buy a key, and they’re still not cheap.
- If you lose the key or it’s stolen, you’ll lose access to your accounts unless you have a backup.
- Although generally considered secure, hardware-based 2FA such as YubiKeys aren’t immune from hacking(new window).
2FA push notifications
Some platforms now send 2FA access requests, known as push notifications, directly to your phone or computer. You simply have to review the request and reply with Yes or No, as in the example from Google below.

No need to install an app, enter a code, or buy a security key. Push notifications are considered one of the most secure 2FA methods because:
- The website or app sends the notification through a secure connection directly to your device, considerably reducing the risk of interception.
- Notifications may also include details about the login attempt for added security — where you are, the device you’re using, etc. (see the Google example above).
However, the two main disadvantages of push notifications are:
- Your phone needs to be connected to the internet to receive the notification.
- With so many popup notifications on your phone, it’s easy to approve a notification automatically without checking the details.
Biometric 2FA
Biometric 2FA, where you yourself are the security token, is becoming increasingly common. Your fingerprints, voiceprint, or a scan of your face, iris, or retina can all be used to prove it’s you logging in.
For example, many banking apps allow you to use Touch ID on iPhone or Fingerprint Unlock on Android to access your bank account once you’ve entered your login credentials.
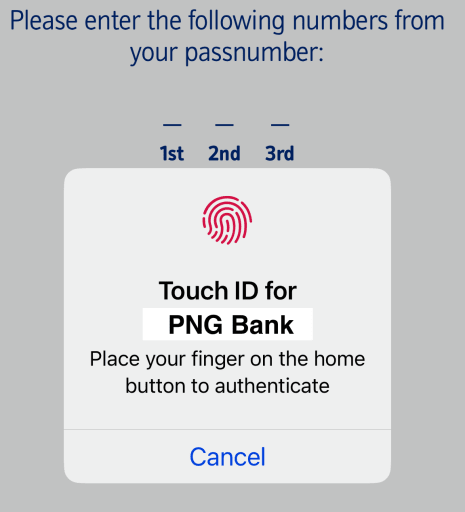
Biometric verification is often used to provide a third way of verifying your identity for multi-factor authentication (MFA).
Since biometric data is difficult to spoof, it’s also increasingly used to provide access methods that eliminate the use of passwords altogether, also known as passwordless authentication(new window).
However, biometric authentication is not without risk. If a biometric 2FA system gets hacked and your fingerprint or face scan is leaked or replicated, you can’t change them.
What’s the difference between 2FA and MFA?
Two-factor authentication (2FA) is a kind of multi-factor authentication (MFA).
2FA requires you to verify your identity in two ways to log in to an account. MFA simply means you have to verify your identity at least twice to log in — usually in three ways.
For example, to log in with MFA, you may have to:
- Enter a password
- Answer a security question
- Provide a fingerprint, enter a passcode from an authenticator app, or use a physical security key
Organizations that require a higher level of security use MFA. For example, banks, healthcare facilities, and government agencies often require you to set up MFA when you register with them.
How to enable 2FA
More and more websites and apps now offer at least one method for 2FA. Here’s how to set up 2FA for Proton and other major tech platforms.
Enable Proton 2FA
To switch on 2FA and set up an authenticator app with your Proton Account:
- Sign in to your Proton Account at account.proton.me.
- Click Settings → All settings → Account and password → Two-factor authentication and switch on the Authenticator app switch.
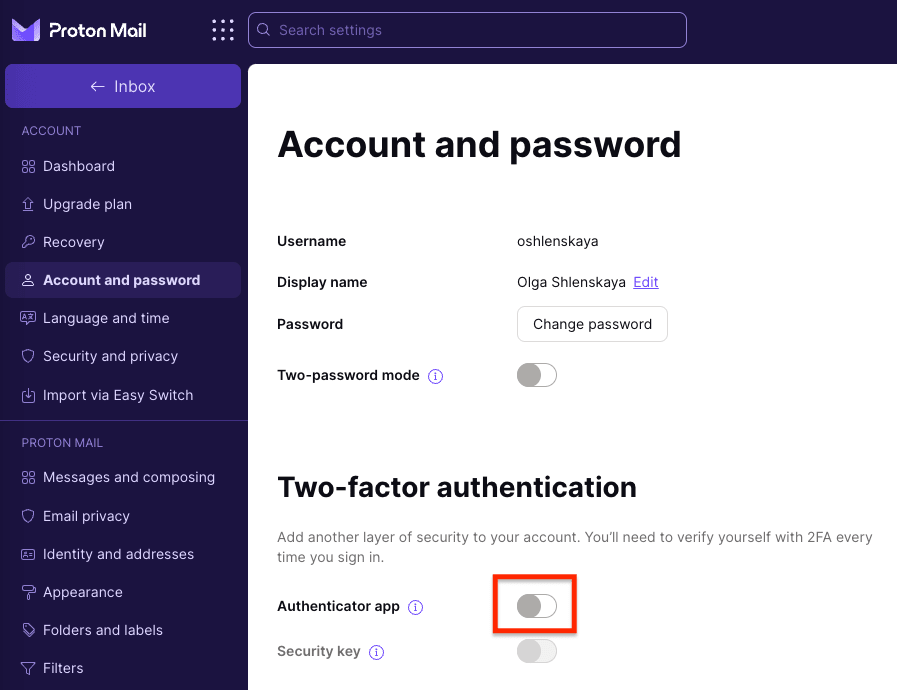
- Follow the onscreen instructions to complete the setup.
Learn how to set up 2FA with Proton
You can also set up a 2FA security key with Proton.
Enable Google 2FA
Google calls 2FA two-step verification. To turn on two-step verification for your Google Account:
- Sign in to your Google Account at myaccount.google.com(new window).
- From the left-hand menu, select Security.
- Go to Signing in to Google, and select 2-Step Verification.
- Follow the onscreen instructions to complete the setup.
When you set up your authenticator app, Google prompts you to use the Google Authenticator app. But you can use any app that supports TOTP.
Enable Apple 2FA (iPhone/iPad/Mac)
To enable 2FA for your Apple devices:
- Sign in with your Apple ID at appleid.apple.com(new window).
- Answer your security questions, then click Continue.
- When you see a prompt to upgrade account security, click Continue.
- Click Upgrade Account Security and follow the onscreen instructions.
You can also enable 2FA using your iPhone, iPad, or Mac(new window).
Enable Microsoft 2FA
Microsoft calls 2FA two-step verification. To turn on two-step verification for your Microsoft account:
- Sign in to your Microsoft account at account.microsoft.com(new window).
- Go to Security → Security basics → Advanced security options.
- Under Two-step verification, choose Set up two-step verification to turn it on.
- Follow the onscreen instructions to complete the setup.
As with Google, Microsoft prompts you to use its own authenticator app (Microsoft Authenticator). But you can use any authenticator app that supports TOTP.
2FA backup codes
If you use an authenticator app on a mobile device or 2FA security key, and your device is lost, stolen, or otherwise compromised, you can lose access to your accounts. That’s why most sites offer you 2FA backup codes — a passcode (or a number of passcodes) you can use to log in if your 2FA methods fail.
Download or print the passcodes and keep them in a safe place. You can also take hard-copy passcodes with you if you’re traveling where the mobile signal or battery charging is unreliable.
For important accounts, it’s a good idea to set up more than one 2FA method where possible, so that if one fails, you can use the other one.
Is 2FA secure?
No login method is 100% secure, but using any form of 2FA is considerably more secure than using a password alone.
But not all 2FA methods are created equal. We recommend using authenticator apps and/or security keys for 2FA, not SMS, which can be intercepted.
Biometrics, like fingerprints and face recognition, are also generally considered safe to use. However, if you live in the United States, it’s still not clear whether a court can force you to unlock your device with biometrics(new window).
Whatever 2FA method you use, it’s only as strong as the weakest link, and that’s usually the password. In the future, online platforms will likely move to authentication methods that use one highly secure factor that’s not knowledge-based, eliminating passwords altogether(new window).
For example, Apple has introduced passkeys(new window), which use Face ID or Touch ID to identify you when you sign in to supporting websites and apps — no password required. Passkeys are highly secure, as they live on your devices and are cryptographically linked to the website or app they’re created for.
Use 2FA everywhere
More and more websites and apps are offering two-factor authentication to secure your personal data online.
While some 2FA methods, like SMS, are less secure than others, any 2FA is much safer than using a password alone. So enable 2FA wherever you can, and choose the most secure and convenient method for you.
When you set up 2FA for accounts, don’t forget to download or print backup codes where they’re available. Many platforms, like Proton, also allow you to set up 2FA with an authenticator app and a security key, so you always have a backup.
If you want to further protect your privacy online, why not secure your personal information with a free Proton Account? With end-to-end encrypted Proton Mail, Proton Calendar, Proton Drive, and Proton VPN(new window), no one but you can access your data. Not even Proton. Stay secure!







