Almost everything on the internet is encrypted these days. And yet data breaches still frequently spill sensitive files into the hands of hackers, and identity theft is a multi-billion-dollar industry. Why?
This article explains what’s broken about most file-sharing systems and how you can start sharing encrypted files more securely, whether in your personal life or for your business.
Why secure file sharing matters
What is encrypted file sharing
Choosing an encrypted file-sharing method
How to send encrypted files
Sharing passwords for encrypted files
Why secure file sharing matters
If you consider the risks of unsecure file sharing alongside the ease of using encryption, it’s obvious that everyone should be using strong encryption to share data on the internet. Globally, the average cost of each data breach is $4.35 million.
And yet most people still rely on services that don’t use end-to-end encryption to send files, such as Google products, Dropbox, WeTransfer, and others.
Here are some of the risks involved with file sharing using unsecure methods:
- Nearly half of data breaches happen in the cloud — Research by IBM(new window) determined that 45% of data breaches affected files stored in the cloud. In other words, documents stored on internet-connected servers were able to be decrypted and stolen. This risk can be mitigated by using end-to-end encrypted cloud services and two-factor authentication.
- Identity theft is common — One study(new window) found that identity fraud scams cost 42 million Americans $52 billion in 2021. One of the most common ways scammers obtained people’s personal data was by enticing them to share it by phone, email, or text message. Using unencrypted methods to send sensitive information is a major red flag.
- Hackers’ best weapon is stealing passwords — The same IBM study found that compromised credentials remain the most popular attack vector for hackers. The good news about that is users can greatly improve the security of their file sharing by using services that focus greatly on account security.
In the next section, we’ll describe a better way to send files over the internet: encrypted file sharing.
What is encrypted file sharing?
Most data on the internet is stored and transmitted using some form of encryption. Encryption is a way of locking files so that only people with the correct key can open them. But different online service providers have different methods of storing those keys. And most platforms keep a key for themselves, including Google, Microsoft, Dropbox, Box, and others.
The most secure form of cloud encryption is called end-to-end encryption, which ensures only you and the person you share a file with can access it. Not even the service provider has a key to unlock the file.
Choosing an encrypted file-sharing method
There are many ways to send encrypted files, ranging from removable storage (e.g. encrypting files onto a USB drive) to file transfer protocol (mostly used by developers).
For most people, the simplest way to send files is by email attachment or cloud storage. There are pros and cons of each choice:
Sharing files via email attachment
Probably the most common way to send files is by email.
Pros: The biggest benefit is convenience. You can deliver the file directly to the person you’re sending it to.
Cons: But all email providers have file size limits on their attachments. Both Gmail and Proton Mail cap attachments at 25 MB. Another drawback is security. Most email providers don’t use end-to-end encryption, meaning they can access your files.
Proton Mail protects attachments with end-to-end encryption, but there’s still a limit on the size of your files.
Sharing files via cloud storage
For sharing large files or folders, people usually turn to a cloud storage provider. Many email services also offer cloud storage for this reason.
The only negative aspect of most cloud storage providers is security. As mentioned, most major cloud storage platforms are not end-to-end encrypted.
Proton Drive has no such drawback. Every file is encrypted on your device using your private key before being uploaded to servers in Switzerland, where user accounts are protected by strong privacy laws.
Once uploaded, it’s simple to send encrypted files to anyone using a password-protected sharing link.
How to send encrypted files
Sharing encrypted files in Proton Drive is similar to sending them on many other platforms. All the sophisticated encryption takes place automatically. Both the contents of the files and the metadata, such as the names of your files and folders, are end-to-end encrypted.
Here’s how to start sharing encrypted files for free with Proton Drive:
1. Sign up for Proton Drive. Be sure to enable two-factor authentication for your account. (Remember, compromised credentials are the most common way hackers access accounts.)
2. Log in to drive.proton.me(new window) and click on New in the top left corner. Then upload the file or folder you wish to share.

3. Once the file is uploaded, click the box to the left of it to select it. Click Get link to create a shareable link. Note that only individual files or folders can be shared with a single link, but multiple files can be grouped into a folder and shared using a single link.

4. The Share via link window will appear containing a secure link that you can copy and paste to share with your recipient via email or message.
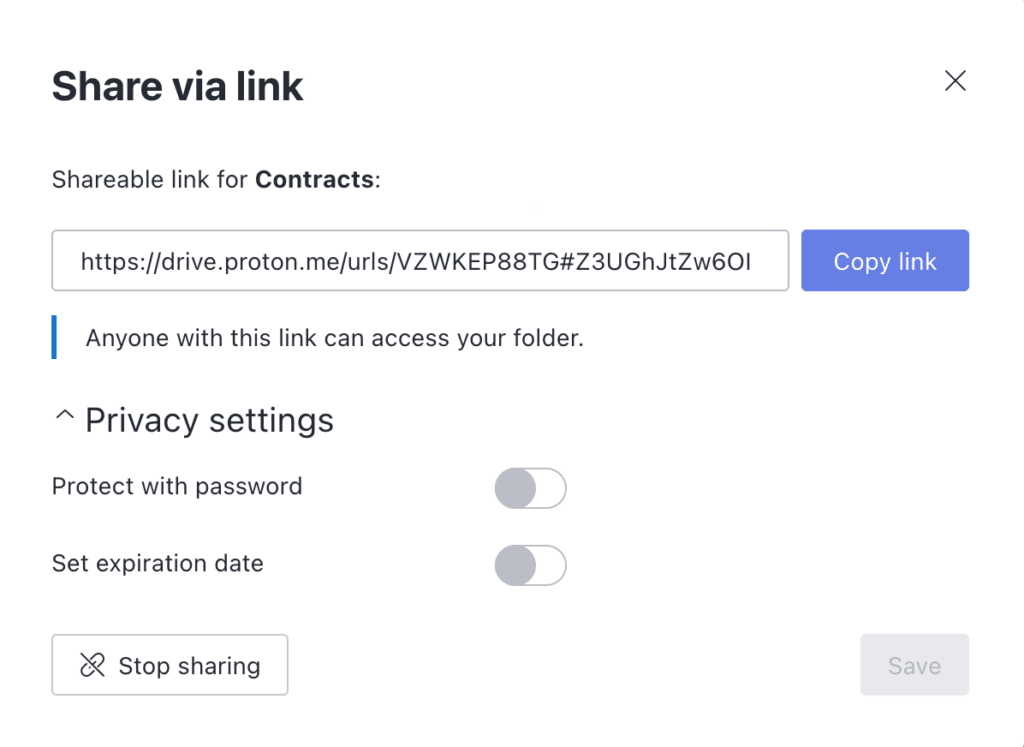
This window contains other privacy settings you can use to further protect your message. You can set an expiration date after which the link will no longer function. You can also set a password that your recipient will need to enter to access the file.
If you set a password, this is what your recipient will see when they visit your link:

Sharing passwords for encrypted files
If you set a password for your files, you obviously shouldn’t communicate the password to your recipient in the same message where you send the sharing link.
The safest way to tell someone the password is in person or by phone. The second safest way is by encrypted message. Here are our favorite secure messaging apps.
(Note that you shouldn’t send the password in a separate email. If your recipient’s email account is compromised, the attacker will have access to both messages.)
Sending encrypted files is simple
As recently as 10 years ago, sending files using end-to-end encryption was too difficult for most people. It involved multiple technical steps and extra software, so few people did it.
Today it’s just as easy to share a file with end-to-end encryption as it is without. But most tech companies don’t implement end-to-end encryption for their users because profiting from users’ data is part of their business model.
At Proton, privacy is our business model. We’re working toward an internet where your data is protected by default. You can join the movement by sharing your files securely and privately with Proton Drive.







