Whenever we develop a service, our goal is to make sure it does not leak or expose any of your information at any time to anyone, including ourselves. This is a radically different approach to most Big Tech offerings, where data collection is the true purpose of the service. This approach also means we often have to create entire new frameworks to handle what otherwise might seem like a simple function.
In this article, we explain how Proton Drive downloads your files so that you receive them quickly while making sure your information remains private and encrypted, even from us.
How other cloud storage services download your files
Before we can explain how Proton Drive downloads your files, we’ll need to look at how most cloud storage services download files.
In the early days of the internet, servers handled the vast majority of the “work” (data processing, encryption, etc.), and web apps did relatively little beyond relaying information to the user.
As the internet developed, applications became more complex and handled more of the processing themselves on the user’s devices. While this allows for more functionality, it comes with a downside. Instead of being able to use the massive amounts of memory and computational power of a server in a data center, the application is bound by the amount of memory, features, and computational power of the device it’s running on.
Current app development is a balancing act between what tasks the server will handle and what tasks the client (or app) will handle.
This brings us to your standard cloud storage service. The simplest way to fetch an encrypted file is to:
- Have the frontend client, such as your browser, initiate a request and have the backend server deal with it.
- The backend server finds the files, creates an archive (if needed), and sends everything back to your browser as a file download.
In this example, your cloud storage service’s backend server does most of the work. Your browser simply receives the file.

This system, while efficient and direct, requires the server to be able to decrypt your files. This simply does not meet Proton’s standard for privacy.
Proton Drive decrypts files locally and doesn’t have access to your data
Our focus on privacy means we do not want any unencrypted data sent to our servers. Consequently, we have our client handle computational work that other cloud storage services can delegate to their centralized servers.
As a result, the way Proton Drive fetches files looks more complex. If the file being downloaded is small, a download on Proton Drive uses the following process:
- The frontend client (your browser) initiates the request.
- Proton Drive fetches all the related data and sends it in an encrypted state to your browser.
- Your browser (the client) decrypts the data, buffers it in memory, and creates an archive that’s then sent out as a classic download.
This way, the Proton server never interacts with unencrypted data or the unencrypted keys that would allow us to decrypt your data. Your client (your browser) handles this entire process. This solution is fast, robust, and straightforward, and the user experience is nearly the same as a standard download.

While this file fetch system works, it is not scalable. We only do this with small files because the size of the file you can download is constrained by the device’s memory, which can vary from device to device. If you’re trying to download 10 GB of files on a device that only has 8 GB of memory, it will simply not work.
Proton Drive “streams” encrypted data to avoid memory constraints
If you want to download a large file (or a lot of files at once), Proton Drive uses another approach: a streaming solution with service workers, which are a type of web worker. A web worker is a web technology that’s used to do work in the background. They let browsers do heavy data processing without freezing or locking up.
A service worker is a special type of web worker that also runs in the background, but it has an important ability: it can act as a proxy, essentially a “middle” layer that can be used for caching. As discussed earlier, a browser can’t create and download a stream without storing the entire file in its device’s memory. Using service workers allows us to work around this limitation. The process of downloading a large encrypted file (or many encrypted files at once) from Proton Drive looks like the following:
- The client (your browser) initiates the request.
- Proton Drive fetches all the related data and sends it in an encrypted state to a web worker on your browser.
- The web worker receives each bit of data, decrypts it, verifies the signature on the file(s), creates an archive (if it’s multiple files), and sends it along in a stream to a service worker. At no point is the entire download compiled or buffered, so it doesn’t matter how much memory your device has.
- The data then passes through the service worker in a streaming fashion and is sent to your browser as a standard download.
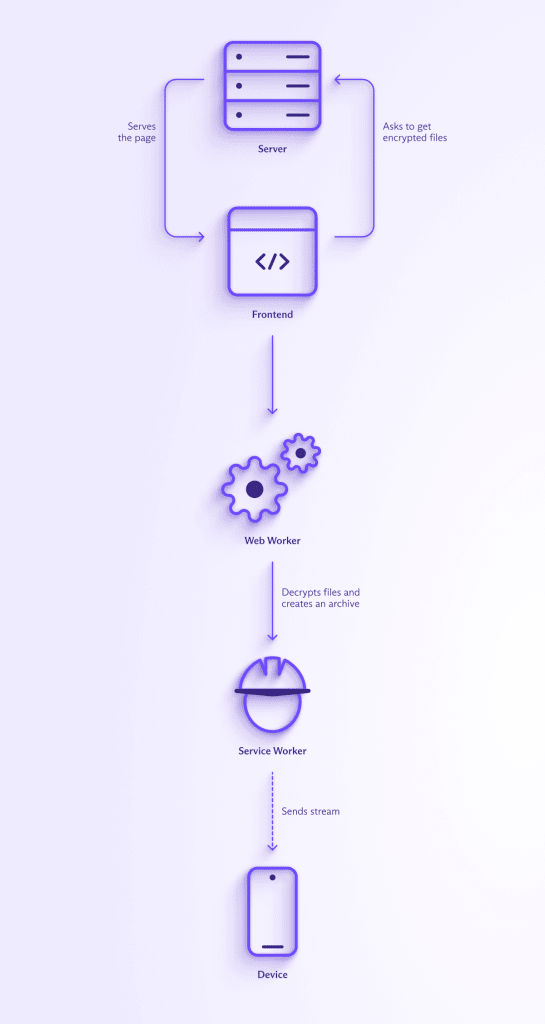
This process is clearly more complex than normal file downloads, but we have done this extra engineering because we’re committed to your privacy. The use of encrypted data streams is an additional complexity, but an important one because it allows Proton Drive to handle much larger files than most other end-to-end encrypted cloud storage solutions. In fact, the only limit on the size of your download is the amount of storage that comes with your Proton Drive plan (and, of course, your device’s storage capacity).
This system led to a longer development time for Proton Drive, but it enables a more seamless user experience, with the download experience being virtually indistinguishable from unencrypted cloud storage services.
Taking security to the next level with digital signatures
With Proton Drive, we don’t just encrypt your data — we also sign it. We have several signatures to protect our users from possible MITM attacks, including from us. These signatures prove that the data has not been altered, intercepted, or replaced. Checking those signatures on the fly is part of the streaming download process as well.
If we discover an issue, such as a missing or incorrect signature (which could lead to a garbled file or is a sign of a tampered file), we’ll pause the download and show you a pop-up dialog that asks if you want to continue.
Proton Drive – Better cloud storage for a better internet
As you can see, Proton Drive does not simply use the same technology as standard cloud storage services. Our focus on making sure you remain in control of your data at every step while also wanting to deliver seamless, fast service means we must build our own process from the ground up. This can make development tricky, but it’s what is necessary to build the world’s most secure and private cloud storage.
As always, we welcome your comments and suggestions on Facebook(new window), Twitter(new window), or Reddit(new window),







